 1.
Web-based Systems Work. From Shanghai to Newark, in hundreds of offices,
schools, museums, data centers, and other buildings, web-based systems are
taking care of day-to-day building operations while giving their owners
unparalleled access in the process. These systems provide all the functions of
a conventional building automation system, including direct digital control of
equipment, trending, scheduling, alarming, reporting, and interfacing with
other building systems. Unlike conventional systems, however, the user
interface is not limited to a few dedicated workstations running proprietary
software. Web-based systems generate conventional web pages as the user
interface, allowing users to log into the system and perform any required
function from any computer on the network. If the network includes the World
Wide Web, this means virtually any computer in the world can serve as the
operator workstation. If the network includes a Wireless Service Provider, WAP-enabled
cell phones and other wireless devices can also be used to access the building
system. Obviously these systems also provide a high degree of security to
prevent unauthorized access, but authorized users can gain significant
productivity improvements from this increased access. Since these systems
provide all the functions of a conventional automation system, there is no
drawback to this increased access. The custodian of a small public school
which has no Internet access can use a dial-up connection to access his system
from his home computer, checking on alarms and making needed adjustments
without leaving the house. For him, the advantage of a web-based system is
that it does not require him to buy multiple copies of proprietary software
from the system manufacturer to install on his work computer, his home
computer, his neighbor's computer, his wife's laptop, or any other computer he
may be near when an alarm comes in on his pager. At the other extreme,
customers with world-wide operations can use these systems to access multiple
facilities scattered around the globe. Not only does the web access allow them
to bring all their facilities together into a unified system, it allows energy
managers and consultants located anywhere in the world to access these
buildings remotely to study energy usage and "fine tune" the
building operation.
1.
Web-based Systems Work. From Shanghai to Newark, in hundreds of offices,
schools, museums, data centers, and other buildings, web-based systems are
taking care of day-to-day building operations while giving their owners
unparalleled access in the process. These systems provide all the functions of
a conventional building automation system, including direct digital control of
equipment, trending, scheduling, alarming, reporting, and interfacing with
other building systems. Unlike conventional systems, however, the user
interface is not limited to a few dedicated workstations running proprietary
software. Web-based systems generate conventional web pages as the user
interface, allowing users to log into the system and perform any required
function from any computer on the network. If the network includes the World
Wide Web, this means virtually any computer in the world can serve as the
operator workstation. If the network includes a Wireless Service Provider, WAP-enabled
cell phones and other wireless devices can also be used to access the building
system. Obviously these systems also provide a high degree of security to
prevent unauthorized access, but authorized users can gain significant
productivity improvements from this increased access. Since these systems
provide all the functions of a conventional automation system, there is no
drawback to this increased access. The custodian of a small public school
which has no Internet access can use a dial-up connection to access his system
from his home computer, checking on alarms and making needed adjustments
without leaving the house. For him, the advantage of a web-based system is
that it does not require him to buy multiple copies of proprietary software
from the system manufacturer to install on his work computer, his home
computer, his neighbor's computer, his wife's laptop, or any other computer he
may be near when an alarm comes in on his pager. At the other extreme,
customers with world-wide operations can use these systems to access multiple
facilities scattered around the globe. Not only does the web access allow them
to bring all their facilities together into a unified system, it allows energy
managers and consultants located anywhere in the world to access these
buildings remotely to study energy usage and "fine tune" the
building operation.
2. Bring your
IT staff into the picture early. Conventional building automation systems
have been network based for many years now, and it is not unusual for them to
utilize the existing IT (Information Technology) network for at least part of
their structure. This has not caused any major problems in the past, but
web-based systems introduce at least two new wrinkles into this
situation:
a. They have the
potential, at least, to provide outside access to the existing IT network,
and
b. They utilize
technologies and devices such as web servers, routers, and IP addressing,
which are traditionally the province of the IT department.
Neither of these issues
is insolvable, and in fact the "solution" is often simply a matter
of providing the IT department with the proper information. They are, however,
reasons to involve the IT staff when planning to install a web-based system,
and it's best to bring them into the picture as early as possible.
[an error occurred while processing this directive]Conventional
control servers tended to use proprietary hardware and proprietary
terminology, which was of little interest to the IT staff. If you wanted to
install an operator workstation and a few primary controllers on their
network, you were no different than the hundreds of other users installing PCs
and network printers. Replace that operator workstation with something called
a Web Server however, and it's an entirely different situation. Now you're
treading on IT territory and they are intensely interested. Their interest is
understandable. Professionally speaking, the IT network is their sole reason
to exist, and they live or die based on how dependable that network is.
Anything that has the potential to disrupt that network is of great interest
to them. In actuality, a properly configured web-based system does not pose a
threat to their network. There are many ways to provide security for a
web-based system, as will be explained in the following section, but it is
important to involve the IT staff in the planning process early so their
concerns can be addressed. If you "surprise" them by hanging a web
server on their network without consulting them in advance, they are bound to
get defensive and create all kinds of obstacles. (The reaction of a mother
bear with cubs that is surprised by the appearance of hikers is nothing
compared to an IT staff that is surprised by the appearance of a web
server.)
3. Address security
concerns early. Whenever a system can be accessed by
"outsiders," security needs to be addressed. There is nothing unique
about web-based control systems in this regard. Indeed, conventional control
systems with dial-up access also have the potential to be "hacked"
by outsiders. In many ways, web-based systems have an advantage over
conventional systems in that they utilize Internet technologies and can take
advantage of the security systems that have been developed to protect bank
transactions, personal information databases, and other sensitive data that is
routinely transmitted over the Internet. The list of customers who use our
web-based system includes universities, military bases, financial
institutions, telecommunication centers, and others who have reason to be
especially careful about security. Again, the key is to involve the IT
security personnel in the planning process, and address their security needs
up front. Factors to consider include:
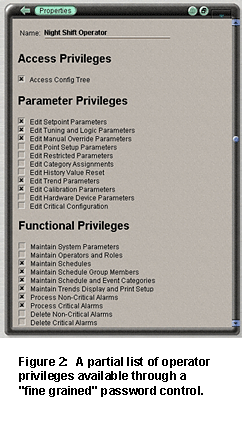 a.
Use a "fine-grained" password protection scheme. Passwords have
long been used as the first line of defense for conventional building
automation systems, and web-based systems are no different. A
"fine-grained" password protection scheme allows you to adjust the
access levels for each individual operator to give them access to the
equipment and properties they need, and to prevent them from accessing
anything else. This type of system will allow you to control access to
setpoints, schedules, tuning parameters, hardware configuration, and other
sensitive functions. Operator privileges can be controlled from "view
only" to full system administrator rights, depending on the needs and
experience of the individual operator.
a.
Use a "fine-grained" password protection scheme. Passwords have
long been used as the first line of defense for conventional building
automation systems, and web-based systems are no different. A
"fine-grained" password protection scheme allows you to adjust the
access levels for each individual operator to give them access to the
equipment and properties they need, and to prevent them from accessing
anything else. This type of system will allow you to control access to
setpoints, schedules, tuning parameters, hardware configuration, and other
sensitive functions. Operator privileges can be controlled from "view
only" to full system administrator rights, depending on the needs and
experience of the individual operator.
b. Use a web server
which is inherently limited. There are "general purpose" web
servers available on the market which are designed to provide web access to
a wide range of network functions, often as an "add-on" to an
existing database. Unfortunately, the widespread use and wide range of
features of these servers also makes them very popular with hackers. We use
a dedicated web server which is built into our product and which only
provides access to the building automation functions. Additional security is
provided by only activating the port needed to access web pages. (Typically
port 80.) By not activating the ports needed for Telnet, NetBios, FTP and
other network functions, the potential for unauthorized access is greatly
reduced.
c. Use encrypted
transmissions. Secure Socket Layer (SSL) connections can be used to provide
128-bit encryption on all transmissions between the browser and the web
server. This effectively prevents anyone from tapping into your
communications to capture passwords and other sensitive data. SSL is
commonly used to protect Internet credit card transactions, and this same
level of protection should be available on your web-based control
system.
d. Use Firewalls
and/or Virtual Private Networks. The WACS server should be compatible with
external firewalls and Virtual Private Networks (VPN) to provide additional
security. VPN can be configured to restrict access to specific computers
which have been individually configured as a member of the VPN. Computers
which are not a designated member of the VPN cannot connect to the network,
regardless of any passwords or "inside knowledge" the operator may
possess.
e. Restrict your
system to an intranet. While the term "Web Accessible Control
System" implies a connection to the World Wide Web, this connection is
not required in all cases. While not connecting your system to the Internet
does reduce the "access from anywhere" advantage of a WACS, the
system is still available from any computer on the internal network.
Universities, data centers, and other customers with a 24/7 facilities staff
may find this is an acceptable trade-off since their on-duty staff still has
full access to the control system.
The security
arrangements needed for any particular installation will depend on the
security needs of the customer. Not all of the provisions outlined above need
to be implemented in all cases. A careful review of the trade-offs involved
with each option needs to be reviewed when planning for a particular
installation, but the bottom line is that web-based systems can be made as
secure as needed.
4. The use of open
protocols enhances the interoperability of WACS. Web-based systems
typically utilize Internet standards such as HTML for generating and
transmitting web pages. These Internet standards are designed to render
computer data as text and graphics which can be understood by humans. While
this allows operators to access multiple systems through a single web browser,
these Internet standards do not provide interoperability between different
pieces of equipment within the building automation system. Fortunately, WACS
can be fully compatible with existing standard protocols for equipment, such
as BACnet, LonWorks, or Modbus. Using these protocols within the WACS greatly
simplifies the integration of equipment made by different manufacturers into a
unified system, and the WACS interface makes this system available through a
web browser. Status values, setpoints, PID gains, and other commonly accessed
values can be presented in a unified front end that shields the operator from
having to learn a different interface for each vendor. BACnet adds higher
level functions such as scheduling, trending, and alarming to this mix, making
it even easier to manage the entire system from a single front end. While all
of these functions can be integrated without the use of an open protocol, the
use of open protocols eliminates the need for custom programming and greatly
simplifies integration. A few examples:
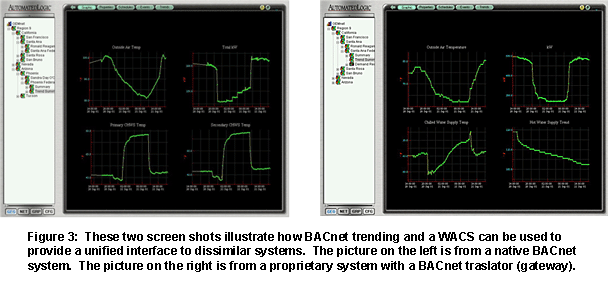
a. A government
facility manager uses BACnet to integrate 11 buildings in 3 states using
control systems made by 4 different manufacturers into a single energy
management system. Five of the buildings were controlled by native BACnet
systems to begin with, while six use proprietary systems which are
translated into BACnet through a gateway. The net result is a unified
interface which allows operators and consultants across the US to view and
manage energy data through their web browsers. (Interestingly, the WACS
system that unifies this network was made by a 5th manufacturer, further
illustrating the interoperability provided by open protocols.)
 b.
The Shanghai ScienceLand Museum, in Shanghai China, uses BACnet to integrate
3,200 control points and 1,000 monitoring points into a single WACS. AHUs,
chillers, pumps, lighting, elevators, fire, security, and other building
systems supplied by 9 different vendors are monitored and controlled by a
unified operator interface.
b.
The Shanghai ScienceLand Museum, in Shanghai China, uses BACnet to integrate
3,200 control points and 1,000 monitoring points into a single WACS. AHUs,
chillers, pumps, lighting, elevators, fire, security, and other building
systems supplied by 9 different vendors are monitored and controlled by a
unified operator interface.
c. The Houston Bush
Intercontinental Airport is using a WACS to integrate two native BACnet
systems plus multiple Modbus systems into a single, unified system. With
construction nearing completion, it is safe to say this integration could
not have been completed within the time and budget available without the use
of open protocols.

 1.
Web-based Systems Work. From Shanghai to Newark, in hundreds of offices,
schools, museums, data centers, and other buildings, web-based systems are
taking care of day-to-day building operations while giving their owners
unparalleled access in the process. These systems provide all the functions of
a conventional building automation system, including direct digital control of
equipment, trending, scheduling, alarming, reporting, and interfacing with
other building systems. Unlike conventional systems, however, the user
interface is not limited to a few dedicated workstations running proprietary
software. Web-based systems generate conventional web pages as the user
interface, allowing users to log into the system and perform any required
function from any computer on the network. If the network includes the World
Wide Web, this means virtually any computer in the world can serve as the
operator workstation. If the network includes a Wireless Service Provider, WAP-enabled
cell phones and other wireless devices can also be used to access the building
system. Obviously these systems also provide a high degree of security to
prevent unauthorized access, but authorized users can gain significant
productivity improvements from this increased access. Since these systems
provide all the functions of a conventional automation system, there is no
drawback to this increased access. The custodian of a small public school
which has no Internet access can use a dial-up connection to access his system
from his home computer, checking on alarms and making needed adjustments
without leaving the house. For him, the advantage of a web-based system is
that it does not require him to buy multiple copies of proprietary software
from the system manufacturer to install on his work computer, his home
computer, his neighbor's computer, his wife's laptop, or any other computer he
may be near when an alarm comes in on his pager. At the other extreme,
customers with world-wide operations can use these systems to access multiple
facilities scattered around the globe. Not only does the web access allow them
to bring all their facilities together into a unified system, it allows energy
managers and consultants located anywhere in the world to access these
buildings remotely to study energy usage and "fine tune" the
building operation.
1.
Web-based Systems Work. From Shanghai to Newark, in hundreds of offices,
schools, museums, data centers, and other buildings, web-based systems are
taking care of day-to-day building operations while giving their owners
unparalleled access in the process. These systems provide all the functions of
a conventional building automation system, including direct digital control of
equipment, trending, scheduling, alarming, reporting, and interfacing with
other building systems. Unlike conventional systems, however, the user
interface is not limited to a few dedicated workstations running proprietary
software. Web-based systems generate conventional web pages as the user
interface, allowing users to log into the system and perform any required
function from any computer on the network. If the network includes the World
Wide Web, this means virtually any computer in the world can serve as the
operator workstation. If the network includes a Wireless Service Provider, WAP-enabled
cell phones and other wireless devices can also be used to access the building
system. Obviously these systems also provide a high degree of security to
prevent unauthorized access, but authorized users can gain significant
productivity improvements from this increased access. Since these systems
provide all the functions of a conventional automation system, there is no
drawback to this increased access. The custodian of a small public school
which has no Internet access can use a dial-up connection to access his system
from his home computer, checking on alarms and making needed adjustments
without leaving the house. For him, the advantage of a web-based system is
that it does not require him to buy multiple copies of proprietary software
from the system manufacturer to install on his work computer, his home
computer, his neighbor's computer, his wife's laptop, or any other computer he
may be near when an alarm comes in on his pager. At the other extreme,
customers with world-wide operations can use these systems to access multiple
facilities scattered around the globe. Not only does the web access allow them
to bring all their facilities together into a unified system, it allows energy
managers and consultants located anywhere in the world to access these
buildings remotely to study energy usage and "fine tune" the
building operation.  a.
Use a "fine-grained" password protection scheme. Passwords have
long been used as the first line of defense for conventional building
automation systems, and web-based systems are no different. A
"fine-grained" password protection scheme allows you to adjust the
access levels for each individual operator to give them access to the
equipment and properties they need, and to prevent them from accessing
anything else. This type of system will allow you to control access to
setpoints, schedules, tuning parameters, hardware configuration, and other
sensitive functions. Operator privileges can be controlled from "view
only" to full system administrator rights, depending on the needs and
experience of the individual operator.
a.
Use a "fine-grained" password protection scheme. Passwords have
long been used as the first line of defense for conventional building
automation systems, and web-based systems are no different. A
"fine-grained" password protection scheme allows you to adjust the
access levels for each individual operator to give them access to the
equipment and properties they need, and to prevent them from accessing
anything else. This type of system will allow you to control access to
setpoints, schedules, tuning parameters, hardware configuration, and other
sensitive functions. Operator privileges can be controlled from "view
only" to full system administrator rights, depending on the needs and
experience of the individual operator.
 b.
The Shanghai ScienceLand Museum, in Shanghai China, uses BACnet to integrate
3,200 control points and 1,000 monitoring points into a single WACS. AHUs,
chillers, pumps, lighting, elevators, fire, security, and other building
systems supplied by 9 different vendors are monitored and controlled by a
unified operator interface.
b.
The Shanghai ScienceLand Museum, in Shanghai China, uses BACnet to integrate
3,200 control points and 1,000 monitoring points into a single WACS. AHUs,
chillers, pumps, lighting, elevators, fire, security, and other building
systems supplied by 9 different vendors are monitored and controlled by a
unified operator interface.