It is important that you know your control system network configuration and keep your documentation up-to-date.
Fred Gordy
Intelligent Buildings, LLC
|
June 2016 |
[an error occurred while processing this directive] |
| Do You Know How and What Your Smart
Building Devices Are Connected To? It is important that you know your control system network configuration and keep your documentation up-to-date. |
Fred Gordy Intelligent Buildings, LLC |
| Articles |
| Interviews |
| Releases |
| New Products |
| Reviews |
| [an error occurred while processing this directive] |
| Editorial |
| Events |
| Sponsors |
| Site Search |
| Newsletters |
| [an error occurred while processing this directive] |
| Archives |
| Past Issues |
| Home |
| Editors |
| eDucation |
| [an error occurred while processing this directive] |
| Training |
| Links |
| Software |
| Subscribe |
| [an error occurred while processing this directive] |
Okay... Your control system was installed a couple of years ago and you were handed riser diagrams, As-Builts, mechanical drawings, etc. and you were good to go. Right?
Maybe...
Up until recently the standard implementation for a controls network was created by the integrator and given either a 192.168.X.X or 10.0.X.X IP schema. In some cases the only way to access the system was from a PC on the same network. In other cases the control network did not touch the corporate network, but it was accessible remotely. This was done by purchasing a router/VPN from a big box electronic store and your ISP (internet service provider) supplied you with a public IP to access your front-end from anywhere in the world.
But is that still the way it is setup?
If it is, is it the right way? Or it may have been set up correctly, but because of zero change management and oversight, your control network and corporate network have converged or holes have been punched in your security.
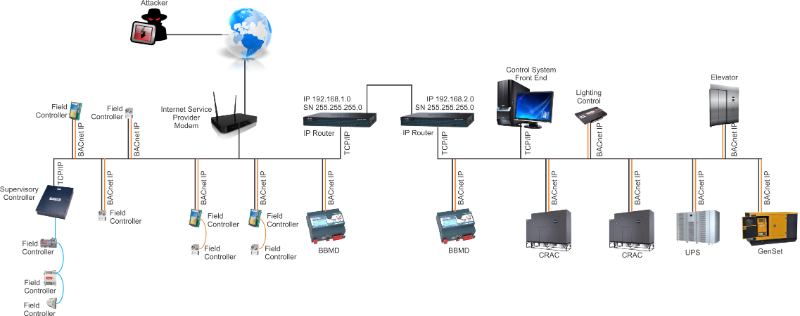
The following examples are possible representations of
what a control network may look like or maybe what is has become after
a few years of "a change here" and "a change there". It is
important that you know your control system network configuration and
keep your documentation up-to-date.
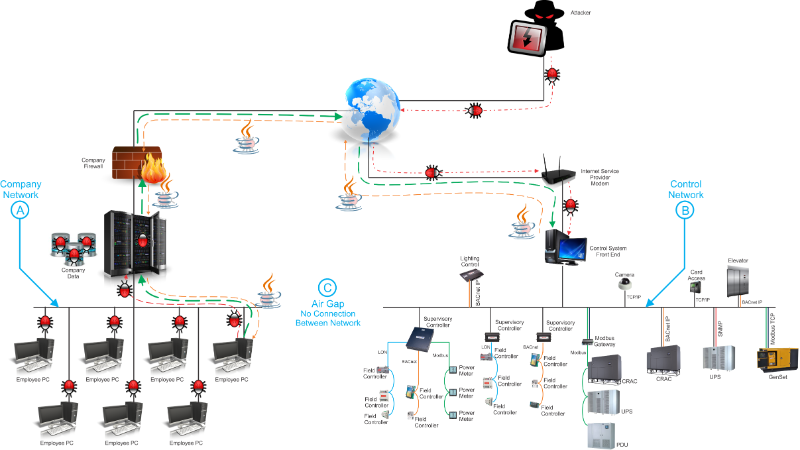
Example 1 - The control network was originally air gapped (physically
separated from the corporate network) and the only access was via a
public IP to front end. The public IP put the control system in
jeopardy by itself. At some point in time a second network card
was added to the front-end and connected directly to the corporate
network. By doing this there is now a hole punched into the
corporate network and it can be used as a pivot point to access company
systems.
Example 2 - The control network and corporate network are air
gapped. There is no physical connection between the two. However,
the control system is exposed to the world with a public IP. The
leaves the control system vulnerable to have infected payloads ready
and waiting for anyone who accesses the system.
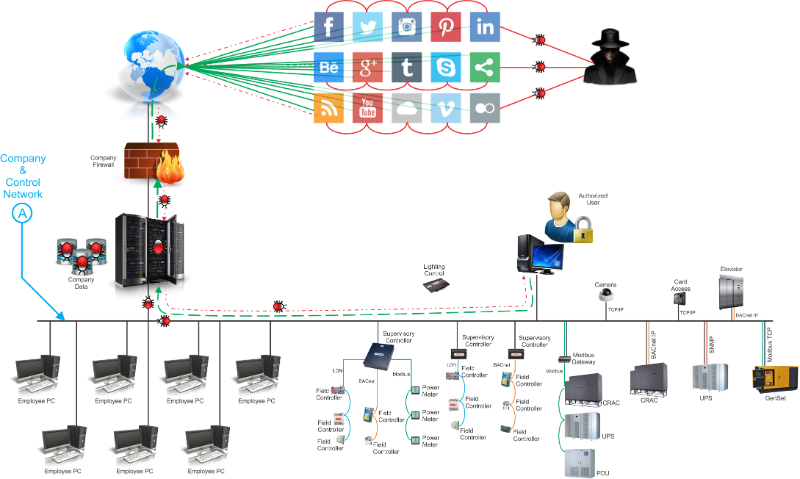
Example 3 - Everything in this example is behind the
corporate firewall and is seemingly safe. It has been my
experience in some cases that the control system front-end is highly
accessible and is used to check email, social media, etc. This
practice can either cause the front-end crash or a means for a threat
actor to inject malware for data mining, command & control, etc.
Example 4 - This example is little different in that
there is a mix of public and private IP's. Certain parts of the
system are exposed and some would think that others are not.
Depending on the system you have, most will allow tunneling, which
means if the bad guy can get to a controller with attached devices,
they can tunnel and command or damage the end devices.
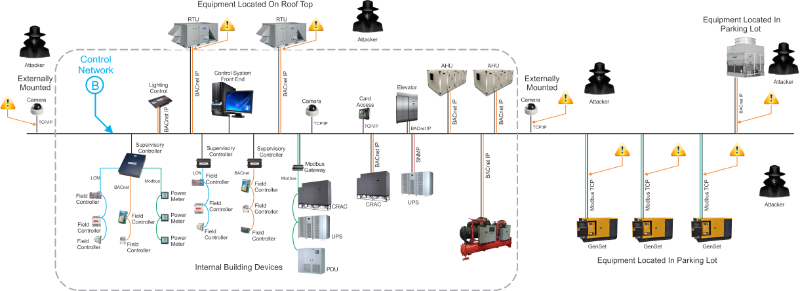
Example 5 - This example deals with the physical security of
a control network. In the example below, equipment with IP
connectivity has been added to the network outside of the
building. Because typically there is never traffic monitoring of
a control network, the bad guy connects something either inline to
remotely access the network from the comfort of their home or
temporarily connect and inject malicious software to perform whatever
task they have chosen.
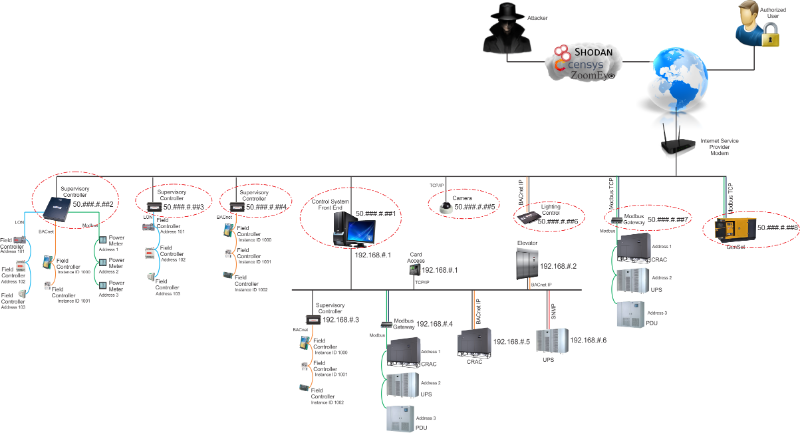
Example 6 - In
this final example, there is a segment of the control network that is
exposed with a public IP and the other segment is on an internal,
private network. At some point someone wanted or needed to get
data from the internal networked control equipment the other network or
vice versa, so they introduce a BBMD to route the traffic across the
different subnet. Using Shodan, Censys, or ZoomEye the bad
will more than likely find the BBMD and then with FREE Bacnet software
scan the network and find the devices on the other side. With
this FREE Bacnet software they now have unrestricted, no password
needed, command and control of these devices.
If you haven't reviewed your control system network architecture in a while, I suggest you do. If you don't have change management in place, you need to. If you have any segment of your control network exposed to the world, work with IT and get it behind a high quality firewall.
The BlackHats are looking and probing and they have plenty of tools available to them to find you. Let's not make it too easy for them.

This year I will
be a part of Intelligent Buildings Boot Camp at IBcon. The
session will take a deeper dive of what is in this article. Plus
it will take you “behind the curtain” to show you the tools that the
bad guys use. I will also show you real-world examples of current
systems that are readily available on the web for the taking. I
hope you will join me on June 21 in San Jose.
[an error occurred while processing this directive]
[Click Banner To Learn More]
[Home Page] [The Automator] [About] [Subscribe ] [Contact Us]