November 2008
![]()
AutomatedBuildings.com
[an error occurred while processing this directive]
(Click Message to Learn More)
November 2008 |
[an error occurred while processing this directive] |
|
|
Steve Rubin, |
The issue of security in industrial buildings was often a secondary issue—on the radar screen, but not the front burner. Safety was always paramount and generally addressed through instrumentation, fail-safe design, documented procedures, training and good management.
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
[an error occurred while processing this directive] |
Today, the world is very different, and security has become the new, high-priority issue. Protecting the operating integrity of a plant, a system, and personnel is now a strategic imperative.
Security measures provide deterrence, detection, and support for forensic (after the event) investigation. Physical security has historically relied on brute-force methods like chain-link fences and door locks. Now a third element, video surveillance, is becoming a sought-after technology to provide the security elements mentioned above. Modern technologies enable real-time video to be integrated into SCADA and HMI systems, Figure 1, in ways that cannot occur via commercial video systems.
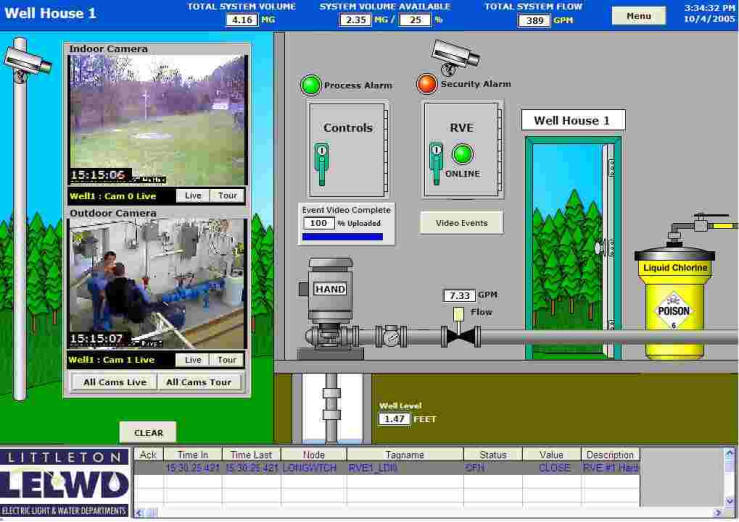
Figure 1: Video can be integrated directly into the HMI screen of a building automation system, so operators and security personnel can see exactly what is happening in critical areas.
For more than two decades industry practitioners have learned that building automation management systems must serve multiple departmental boundaries to deliver the highest value. Designing and deploying relevant security measures must leverage these considerations and production environments.
Under Watch
Leaders focused on protecting their businesses, brand equity, and production
from breach must confront a number of critical dependencies: People
productivity, core processes and procedures, legacy and emerging technologies,
and costs. Deterring the threats and minimizing the impact is even more
challenging for highly distributed, disparate organizations.
The best solutions undergo measurement for total cost of ownership, ease and speed of deployment, and integration while decreasing the burden on your people.
People: Every enterprise must be vigilant, and every employee must share this vigilance. How do you avoid security becoming a silo and a hit toward productivity? Integrating video security into a building management system, Figure 2, provides a common operator interface for production operations, speeding the acceptance of security as an integrated responsibility.
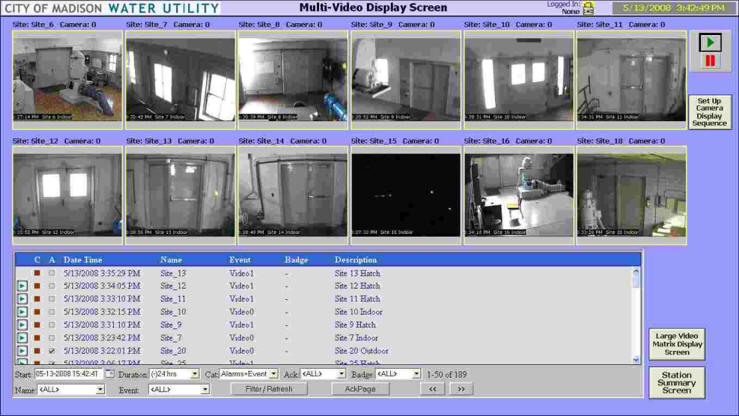
Figure 2: LIve video on the building management HMI screen can show several areas of the plant at one time.
Security Awareness Training is also critical to streamline relevant information and to identify threats and intrusions early. Each group with an enterprise shares the responsibility to keep the organization secure. Security cannot become its own silo or owned by one department such as IT, audit, risk, or others.
Technology: Large organizations have deployed and incorporated a diverse set of physical and logic security and safety technologies spanning more than 30 different technologies. Newer technologies should integrate and make use of existing investment as much as possible without needless upgrades and new capital expenditures.
[an error occurred while processing this directive] Processes/Procedures: Managing the integration, introduction and deployment processes must be simplified and at minimal cost. Automating evasive actions on your most remote unmanned facilities is possible and is best served with technologies designed to handle long-haul remote applications. Solutions that include camera standards, integrated alarming, and event notification over a diverse set of proprietary and often low-bandwidth networks, is critical.
When you take this integrated approach, common alert policies and procedures covering incident notification and response can be refined, distributed, and leveraged—one surveillance system and operator interface for all alerts.
“Attention by exception” is really how most building security systems operate. Guards periodically observe indications, but only take action when an alarm condition occurs, such as an door opening alarm, smoke alarm, intruder alert, and so on.
If a video image of the process unit appeared on the screen when an exception occurred, the operator would be able to immediately see what was happening. This method of operation is much better than the standard “surveillance” approach of watching closed-circuit TV monitors, waiting to pick up visual cues to changes. Studies have shown that humans will lose interest and be unable to detect changes shown on screens if they are forced to stare for more than 20 minutes.
Direct your attention to simplified systems that tightly integrate within your existing building management, SCADA PLC, or RTU architecture. You will benefit from multiple sets of extra eyes wherever you need them operating every second of every day 24x7.
If video can help us discern more about the real conditions, help us see into remote areas, and bring us more information faster…then why has video been so slow to be adopted in building applications? Until recently, all camera technology was analog, and thus it required its own network for operation. Many traditional video systems were originally designed for casinos, parking garages and shopping malls. It was extremely difficult to connect these “closed circuit TVs” to an HMI screen.
But many plants have a much more suitable network, one that’s almost hack-proof, paid for, and reliable: the network for the building automation system, Figure 3. This network was designed to handle digital communications between controllers and computers, and it can easily accommodate video images, too.
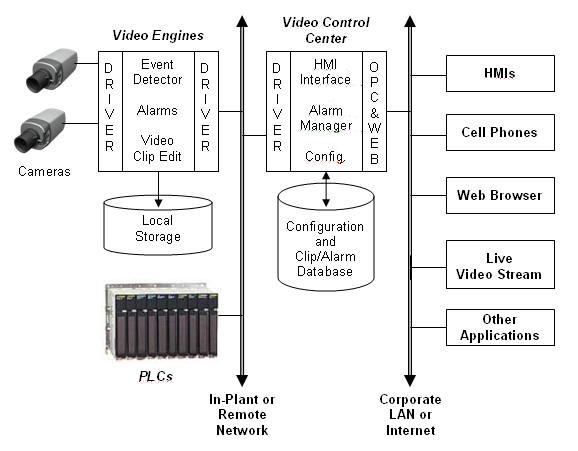
Figure 3: Video images can be transmitted over a building automation system’s network, archived in a data base, and recalled for viewing on HMI screens, cell phones, and web browsers.
Protecting headquarters has been traditionally easier, but the most vulnerable sites are often the most remote. Companies selecting those solutions that cover both the local and remote bases integrated within their existing legacy automation will be the ones that gain an upper advantage.
About The Author
Stephen Rubin is president and chief executive of Longwatch. He was the founder of Intellution, Inc., a developer of process control software for personal computers. His e-mail is srubin@longwatch.com.
[an error occurred while processing this directive]
[Click Banner To Learn More]
[Home Page] [The Automator] [About] [Subscribe ] [Contact Us]