April 2010
![]()
AutomatedBuildings.com
[an error occurred while processing this directive]
(Click Message to Learn More)
April 2010 |
[an error occurred while processing this directive] |
|
|
|
There was a time that the convergence of building automation systems (BAS) across the enterprise network was a novel concept. And much like the first wave of cell phones, early efforts to marry building and information technology (IT) were imperfect and the results a bit clunky. Today, however, BAS-IT convergence is an everyday reality. New Web-based technologies are driving open standards (e.g., XML) that improve ease-of-use by delivering information to those who need it, when they need it, and how they want it, whether it’s a desktop computer or (highly evolved) mobile device.
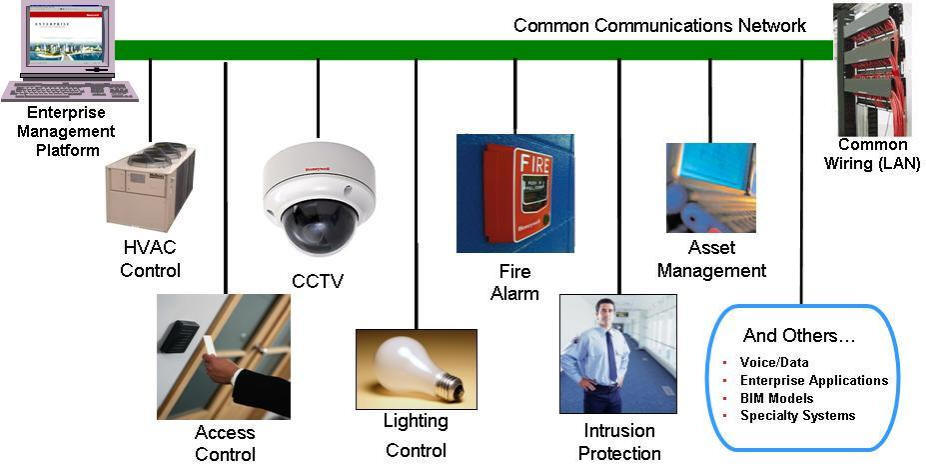
Integrating building systems across the IT backbone is increasingly common;
it’s a shift that brings multiple benefits, as well as new responsibilities.
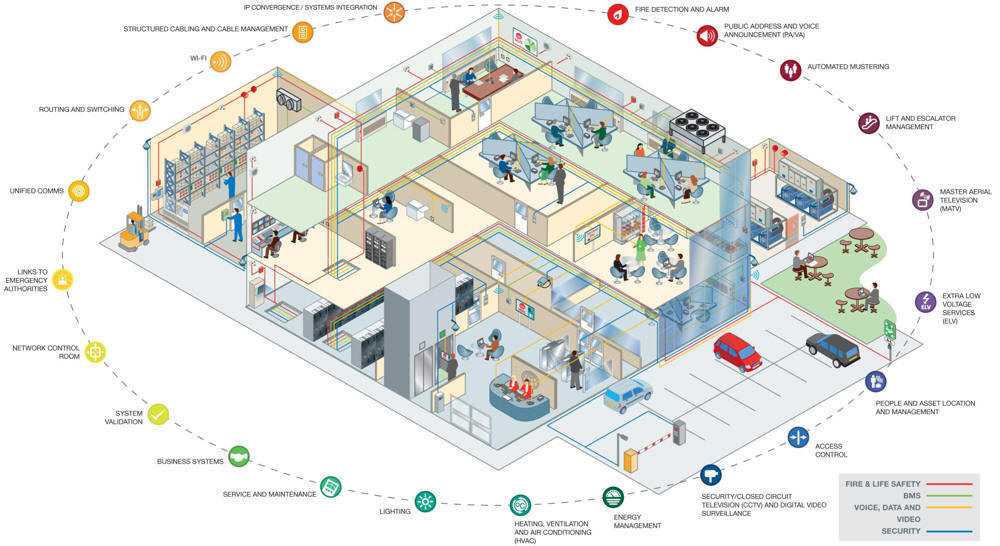
The key advantage to convergence is the ability to aggregate, evaluate and
deliver actionable information to people any where and in any format.
|
|
|
|
|
|
|
|
|
|
|
|
|
[an error occurred while processing this directive] |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
[an error occurred while processing this directive] |
The standardization and rapidly
decreasing cost of connectivity has already delivered benefits to facility
managers and their organizations that range from improved comfort to reduced
energy consumption and costs.
As the concept of convergence has evolved, it has also ushered in a new era of
computing “in the cloud”, enabling organizations to manage building data from
disparate systems across multiple locations using shared applications in a
hosted environment. This cloud architecture delivers additional benefits
including reduced capital expenditure on IT infrastructure and support, while
increasing scalability to address new organizational challenges such as
sustainability, predictive maintenance and asset management
But despite the many advantages, integrating lighting, HVAC, power, video,
access control, fire safety and other systems onto an IT network is not yet
“plug and play.” Like most things in a building, planning, collaboration and a
well defined architecture are keys to accomplishing the transition.
Organizations must adopt an all-encompassing approach to fully seize the
opportunity and ultimately improve the bottom line.
Following is a blueprint for organizations looking to embrace and leverage
convergence — now and into the cloud.
Building a Common Vision
Successful convergence hinges on developing a unified strategy between
traditionally separate groups — facilities, security, safety and IT. Fostering
collaboration and building partnerships among these groups poses several
challenges because each part of the organization has separate (and sometimes
conflicting) priorities and budgets. Establishing common goals, such as
combating rising energy costs, extending asset life, reducing risk or protecting
intellectual property, will help drive this collaboration. Maintaining clear
lines of communication and establishing strong working relationships among these
groups is essential for success.
Integrating building systems and IT means merging roles and responsibilities and
obliterating silos previously in place. This merger, which is the first step
toward integration, is critical and thus requires as much careful planning as
any other strategic component.
The IT relationship should be established during the planning period and is key
to selecting the standards and protocols that can make convergence with other
enterprise systems possible. Initial discussions should include making the
architectural decisions surrounding convergence, the implementation process and
the desired outcomes from data sharing and dashboard management applications. IT
will want to determine what the integrated building systems will bring to a
network, including bandwidth, exposures and data management structures, as well
as how the building resources will interact with other systems already on the
network.
Convergence provides the greatest savings when organizations can start asking
the critical questions for optimal system use and performance: “Where else can
we use this?” and “How can we maximize this?” Questions such as these can help
guide converged systems deployment and performance as groups collaborate to meet
overall business goals.
Protecting Vital Systems
As with any network-based system, security exposure and converged
system vulnerabilities must be properly addressed. Careful planning and
collaboration between facilities groups and IT, however, can help mitigate risk
and enhance security when it comes to the network.
A key productivity improvement of convergence comes from the “anywhere access”
using a Web browser. However, when that includes the use of wireless networks or
remote connectivity, the network security and authentication approach is
critical to keeping the network and all systems secure. When integrating any
building system onto a network, there are several issues that must be addressed.

Wireless technology gives facilities personnel access to diagnostic data and technical documents that can help them address problems quickly and effectively. It’s essential, however, that this technology is deployed using the proper network security and authentication protocols.
First, personnel from all departments — including
facilities, IT, security and safety — need to identify where system exposures
exist based on required functionality. Who will manage network access, for
example? When the traditional departmental lines are redrawn, critical tasks
must be identified and assigned; each group must have a clear understanding of
its roles and responsibilities.
Planning is particularly important when looking at logical exposures. For
example, when plugging an access control system into a network, card readers and
related management software become vulnerable to network threats such as
viruses. Those threats would impact both a company’s security and IT systems.
Conversely, systems on the facilities side can introduce new vulnerabilities to
a network. Like any software, a BAS can become a point of entry for threats if
it is not secure and routinely updated. That’s why many companies are turning to
Web-based support tools — similar to what’s used in the IT realm — that provide
automatic control system updates and security patches, among other things. These
tools help ensure building systems aren’t susceptible to cyber attacks.
Developing a Security Plan
Monitoring is a crucial factor for network security and reliability,
and when facility, security and business systems are all sharing a common
network, the issue becomes especially important.
Depending on available resources, implementing a monitoring system for all
critical network components can ensure fast notification and problem resolution
when issues, such as viruses or unauthorized access, occur.
Besides monitoring, other options for improving security, response and
notification time include integrating functions that have previously existed in
silos. Organizations have benefited from integrating IT security and building
security, not only for operational savings such as a common 24-hour monitoring
center, but also to ensure that intellectual property is as secure as physical
assets.
[an error occurred while processing this directive]
Applying IT Standards to BAS
Integrating a building system with an IT network means standard IT
practices, methods and maintenance now apply to BAS as well. When convergence
takes place, it’s important for facility and security groups to learn and apply
standard IT operating procedures.
Specifically, IT standards include system maintenance practices, notification
procedures and hardware standards. If a network experiences an outage, or a
system on that network goes down, how quickly will facility personnel be
notified, for example? And how will regularly scheduled network maintenance
affect critical building systems? Who will manage security patches for building
systems? Who manages the backups and disaster recovery plans?
To address these questions, all maintenance and system changes must follow a
standard management process, which regulates when and how any action that
affects the network is performed. As part of the process, for instance, those in
charge of building automation might receive notification of scheduled
maintenance, which might let them know they will not be able to adjust the HVAC
system or view certain alarms during a specific time period.
Going forward into the cloud, BAS will join a rich IT services environment that
is standardized, and allow facilities, safety and security teams to focus on
their primary mission without the complexities of managing networks, security,
access, and IT hardware life cycles. IT benefits by leveraging shared assets in
both server and networking infrastructure to provide another set of
mission-critical applications to the business.
Employing Recovery Strategies
Recovery strategies are among the other key IT practices that must be
addressed when integrating building systems onto a network. Placing data from
multiple systems in one location provides several benefits, but also introduces
additional risks. Establishing sound recovery strategies can ensure critical
data isn’t lost and critical system uptime in maintained at the lowest cost.
User error is typically the cause of data loss, and placing data on a network
often means increased user exposure and chances for error. To determine the
appropriate backup strategy, companies must determine how much data loss and
downtime they can afford, as well as how many changes are regularly made to the
data and the frequency with which these changes occur. The answers will vary
based on the type of organization. A commercial office building will have very
different needs from a high-tech organization or a facility that handles U.S.
Department of Defense work.
These factors must then be weighed with the appropriate data cost model,
including labor, space and storage. Cost increases as the amount of stored data
rises. An organization might decide it isn’t willing to lose more than an hour’s
worth of data and will pay the associated storage backup costs.
Once the optimal level of backup is determined, organizations should apply
backup methods for all systems, such as transferring database content to disks
or keeping transaction logs.
Another critical component of a backup strategy is regular testing and
evaluation. Set a reminder each month for testing, for example, and select a
server at random. Restore the data from that server, and then evaluate the
testing results. Did the strategy run smoothly? Did anything unexpected happen?
Establishing these tests and analyzing the results can mean the difference
between smooth convergence and losing mission-critical data.
When the time to recover from backups presents an unacceptable risk or cost,
companies should implement redundancy strategies, which can limit downtime to
mere seconds. While full redundancy used to be a cost that few could justify,
the move to virtualized servers and shared resources makes this a viable option
for most systems.
Moving into the Cloud
As integration of building systems onto IT networks becomes more
commonplace, some organizations have built upon the concept by managing their
building systems and data across multiple locations using a virtualized network
architecture, a step on the evolutionary path called cloud computing.
Cloud computing is a natural extension of convergence, and at a basic level
involves sharing resources such as servers, network infrastructure, software and
applications across a network. This eliminates costly dedicated infrastructure
and the high operating costs that come with it. Having application services and
data hosted and managed through the cloud creates a highly scalable environment
to deliver information to as many users as necessary using a wide array of
devices.
Cloud computing is broadly categorized in two ways, public and private. And when
considering cloud computing, organizations must weigh several factors — such as
reliability, security and how mission-critical the service is to their
organization — to determine which approach fits their needs.
Public clouds closely resemble the application service provider (ASP) model of
the late 1990s, where externally hosted applications are delivered via
subscription to a customer organization. This approach is rapidly gaining ground
with schools, multi-tenant buildings and shopping centers where investment in
and operation of IT infrastructure is not core to the business operation; as a
result, the lower cost of a shared public cloud provides the best value.
Private clouds are hosted behind an organization’s own firewall, and deliver
applications to users within the organization, often through a portal or thin
client such as a Web browser. Many organizations view private clouds as
inherently more secure and easier to manage through network password
credentialing, encryption, and certificate-based security. This approach is most
common for “facilities clouds” at multi-building and even multi-national firms,
where large business-critical IT infrastructures already exist.
From a building automation perspective, a typical cloud computing scenario could
involve an organization purchasing a number of points of automation, with a
service provider managing the off-site server that hosts the system applications
and aggregates data. The building system information is delivered back to the
customer via a dashboard, allowing them to use the data to optimize onsite
infrastructure and inform decision making.
[an error occurred while processing this directive]
Because these applications are delivered as a service in a hosted environment,
updating systems becomes more frequent because it’s easier to make a change in
one place than it is to do it 100 times across multiple locations with disparate
IT environments. Functionality incrementally improves as time goes on too,
especially compared to static standalone systems that require more involved
periodic upgrades.
In addition to reduced infrastructure, and increased flexibility and
performance, one of the key benefits cloud computing provides is the ability to
consolidate information from disparate systems across multiple locations to
solve problems that weren’t able to be addressed before. Many organizations are
developing application-specific clouds, often private, to help with these
challenges.
For example, one Honeywell customer needed to seamlessly aggregate environmental
and energy-efficiency data from across dozens of sites nationwide in support of
its corporate social responsibility (CSR) program. Their reporting process had
proven slow and inefficient, with data collectors at each facility logging the
information on various local systems, then sending to the corporate office for
further analysis.
To streamline the process, the organization employed a cloud-based application
that seamlessly gathered each local system’s data, allowing not only the
corporate office to better manage CSR reporting in a timely manner, but also
enabling the local sites to view and compare progress against their peers in
near real time. The cloud has helped eliminate a non-value added task and
allowed each local facility to remain in control of their data.
As cloud computing becomes more prevalent so will the importance of the facility
manager whose primary focus will be maintaining and optimizing onsite systems,
including mechanical and electrical assets, sensors, actuators and other
building infrastructure. In the end, if equipment and sensors do not provide
accurate data, the sophistication of any IT architecture will not matter and
efficiency goals will not be achieved.
Planning to Get the Desired Results
Cementing roles and relationships, keeping lines of communication
open, and planning for all phases of convergence are imperative if an
organization aims to improve its processes and realize the full value of
integrated systems. Moving to the cloud is simply a new path to further reducing
facility operating costs while ensuring safe, comfortable and productive working
environments.
The thin line between success and failure is characterized by how well an
organization can establish common ground, meet all departmental needs, and
support new ways of thinking and doing. By anticipating requirements and
adhering to common standards, facility, security, safety and IT personnel can
operate in partnership to achieve higher system performance, with lower capital
investment, for optimal business results.
About The Author
Greg Turner is the director of global offerings for Honeywell
Building Solutions. In this role, he is responsible for the research and
development of technology that makes facilities more safe, secure, comfortable
and energy efficient. Greg has been with the company for more than 20 years,
holding a variety of positions from maintenance technician to project engineer.
He can be reached at
greg.turner@honeywell.com.
[an error occurred while processing this directive]
[Click Banner To Learn More]
[Home Page] [The Automator] [About] [Subscribe ] [Contact Us]